Infrastructure protection on AWS is crucial, especially with the ever-evolving threat landscape. On AWS, there are various infrastructure protection services that can help you secure your cloud environment. Some of the key services include:
- AWS Shield: A managed Distributed Denial of Service (DDoS) protection service that safeguards web applications running on AWS. It helps protect your applications against volumetric and state-exhaustion DDoS attacks.
- AWS WAF (Web Application Firewall): Helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. You can use AWS WAF to create custom rules for traffic filtering based on IP addresses, HTTP headers, or URI strings.
- AWS Firewall Manager: A security management service that makes it easier to centrally configure and manage firewall rules across your accounts and applications in AWS Organization. It simplifies your AWS WAF, AWS Shield Advanced, and AWS Network Firewall administration.
- AWS Network Firewall: A managed service that makes it easy to deploy essential network protections for all of your Amazon Virtual Private Clouds (VPCs). It provides granular control over network traffic and allows you to build scalable network security services.
- Amazon GuardDuty: A threat detection service that continuously monitors for malicious activity and unauthorized behavior to protect your AWS accounts and workloads. It uses machine learning to detect anomalies from multiple data sources like VPC Flow Logs, CloudTrail logs, and DNS logs.
These services can be used in combination to provide defense in depth and protect your AWS infrastructure from various security threats. Additionally, leveraging tools like AWS CloudTrail for logging and monitoring, AWS IAM for access control, and AWS Config for compliance can further enhance your infrastructure protection capabilities on AWS.
Example: Implementing an Infrastructure Protection Service with the AWS CLI
One way to protect your infrastructure is by using AWS Network Firewalls, which can help you monitor and control traffic to and from your VPC. If you’re new to the AWS Network Firewall, here is a list of blog posts you should read prior to following my example:
- Deployment models for AWS Network Firewall
- Deployment models for AWS Network Firewall with VPC routing enhancements
If you are familiar with those deployment models, you should understand what we’re going to do.
Here are a few AWS CLI examples to demonstrate how you can work with AWS Network Firewalls.
You will need the following elements to deploy a firewall:
- A Stateless Rule Group
- A Firewall Policy
- The VPC it will be deployed in
- The subnet where the firewall endpoint will be
Create a Stateless Rule Group
Step 1: Define Your Stateless Rule Group in a JSON File
{
"RuleGroupName": "MyStatelessRuleGroup",
"RuleGroup": {
"RulesSource": {
"StatelessRulesAndCustomActions": {
"StatelessRules": [
{
"RuleDefinition": {
"MatchAttributes": {
"Sources": [
{ "AddressDefinition": "0.0.0.0/0" }
],
"Destinations": [
{ "AddressDefinition": "0.0.0.0/0" }
]
},
"Actions": [
"aws:pass"
]
},
"Priority": 1
}
],
"CustomActions": []
}
}
},
"Type": "STATELESS",
"Description": "Example stateless rule group",
"Capacity": 10,
"Tags": [
{
"Key": "ExampleKey",
"Value": "ExampleValue"
}
]
}
This JSON file defines a stateless rule group with one rule that matches all traffic (0.0.0.0/0 for both sources and destinations) and takes the action to pass the traffic.
Step 2: Use the AWS CLI to Create the Stateless Rule Group
With your JSON file ready, run the following command in your terminal to create the stateless rule group:
“
aws network-firewall create-rule-group --cli-input-json file://stateless-rule-group.jsonThis command instructs AWS CLI to create a new rule group based on the definitions in your JSON file.
Once you execute that command you should see an output like the one below.
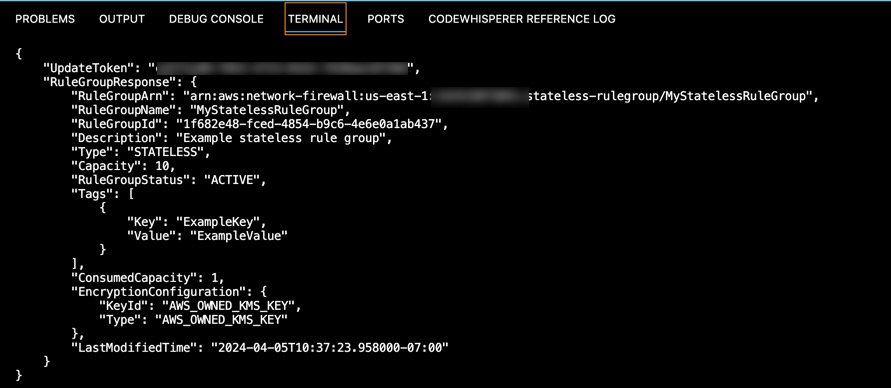
Take note of the RuleGroupARN. You’ll need it in the next step.
Create a Firewall Policy
Now we are going to define the firewall policy in a JSON file:
- Create a JSON file (e.g., firewall-policy.json) that defines your AWS Network Firewall policy. Here is an example of a simple policy note that we reference the ResourceArn of the Stateless Rule group we created:
{
"FirewallPolicyName": "MyFirewallPolicy",
"FirewallPolicy": {
"StatelessDefaultActions": [
"aws:pass"
],
"StatelessFragmentDefaultActions": [
"aws:drop"
],
"StatelessRuleGroupReferences": [
{
"ResourceArn": "arn:aws:network-firewall:us-east-1:1234567890:stateless-rulegroup/MyStatelessRuleGroup",
"Priority": 1
}
],
"StatefulRuleGroupReferences": []
},
"Description": "Your firewall policy description",
"Tags": [
{
"Key": "ExampleKey",
"Value": "ExampleValue"
}
]
}- Use the
create-firewall-policycommand: Execute the following AWS CLI command to create the Network Firewall policy:
aws network-firewall create-firewall-policy --cli-input-json file://firewall-policy.json- Next, verify the creation: After running the command successfully, you will receive a response containing details about the newly created Network Firewall policy, including the policy ARN.
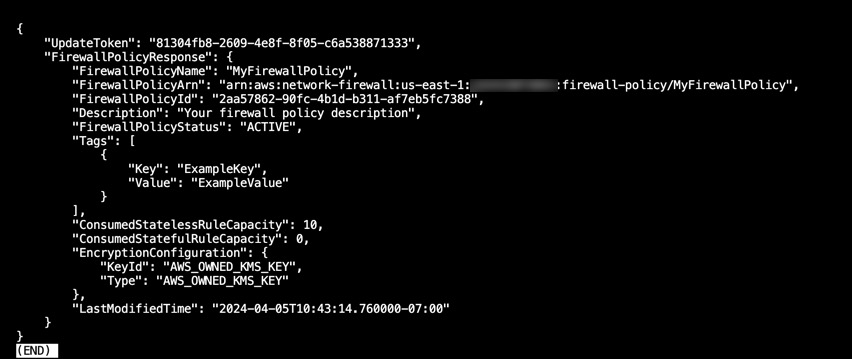
That’s it! You have now created an AWS Network Firewall policy using the AWS CLI.
Now we need to create the Network Firewall.
Create the AWS Network Firewall
To create an AWS Network Firewall you need the ARN of the policy you created, the VPC ID where the firewall will be deployed and the subnet the firewall will be deployed in. Using the following command we can create the firewall.
aws network-firewall create-firewall \
--firewall-name my-firewall \
--firewall-policy-arn arn:aws:network-firewall:us-east-1:1234567890:firewall-policy/MyFirewallPolicy \
--vpc-id vpc-0ae0891d4aeae8506 \
--subnet-mappings SubnetId=subnet-0a3e07fcd0545df5cIt will take a few minutes to provision. You can see this in the AWS Console:
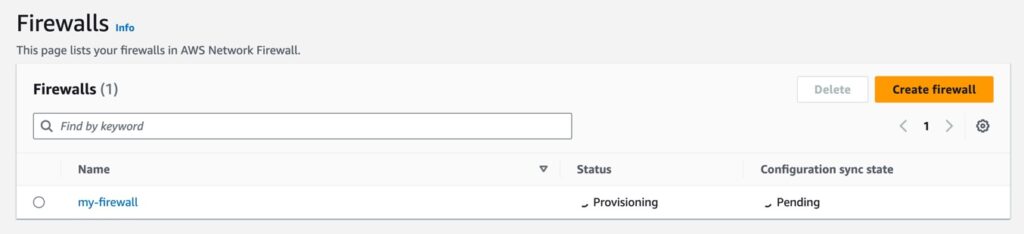
Once the firewall is provisioned you’ll need to make sure traffic is routed properly to send traffic from your private subnet with host host instances, through the firewall subnet with the firewall endpoint, then out to the Internet. I am not going into those details in this post, because the purpose of the post is simply to highlight that there are a few Infrastructure Protection services on AWS, AWS Network Firewall is one of them, and you can deploy it from the AWS CLI.
If you’re interested in building out an entire AWS Network Firewall configuration, please take the time to do the AWS Network Firewall Workshop.
Generative AI and Infrastructure Protection
Now, let’s talk about Generative AI and how it can play a part in infrastructure protection on AWS. Generative AI can be used to analyze network traffic patterns and anomalies, helping in the detection of potential security threats. By training a Generative AI model on normal network traffic, it can learn to recognize deviations from the normal behavior, indicating a potential security breach or attack.
Here’s an idea on how to use Retrieval-Augmented Generation (RAG) could be used with GuardDuty. RAG combines the power of information retrieval and language generation to enhance the capabilities of generative AI models. By fetching relevant information from a database or documents and then using that context to generate responses, RAG models can provide more accurate, informative, and context-aware outputs. In the context of AWS Infrastructure Protection, RAG can be instrumental in several advanced use cases, particularly where decision-making is enhanced by access to a wide range of dynamically changing information.
Use Case: Automated Threat Response and Mitigation
In an AWS environment, security threats can range from DDoS attacks, unauthorized access attempts, to more sophisticated threats like zero-day vulnerabilities. Keeping up with these threats requires constant vigilance and rapid response, something that automated systems can assist with, especially when human response times might not be fast enough.
How RAG Can Help
- Threat Detection and Information Retrieval:
- A RAG model can continuously monitor logs and alerts generated by AWS services like CloudTrail, GuardDuty, and CloudWatch.
- Upon detecting an anomaly or a potential security threat, it can instantly retrieve relevant information from a vast collection of security advisories, white papers, AWS documentation, internal documentation, and known threat databases.
- Contextual Analysis and Threat Assessment:
- Using the retrieved information, the RAG model can assess the context and severity of the detected threat by comparing it against known patterns, vulnerabilities, and exploits.
- This includes analyzing the potential impact of the threat on the infrastructure, considering factors like the affected AWS services, data sensitivity, and compliance requirements.
- Automated Response Generation:
- Based on the analysis, the RAG model can generate recommended actions or automate responses. This could range from isolating affected instances, updating security groups, deploying AWS WAF rules to mitigate DDoS attacks, or initiating backups in response to ransomware threats.
- For complex issues requiring human intervention, the model can draft detailed incident reports, including the threat’s nature, affected resources, recommended mitigation strategies, and reference to similar past incidents and how they were resolved.
Implementing ideas like this can help automate the initial phases of threat detection and response, significantly reducing the time from threat detection to mitigation. It could also offer better context by pulling in relevant data, enabling more informed decision-making for complex security issues. It could also handle the analysis and response generation for multiple threats simultaneously, scaling as threats evolve or increase in volume.
In summary, using RAG for AWS Infrastructure Protection has the potential to allow for a dynamic, informed, and efficient approach to security threat management, combining the best of AI’s analytical capabilities with human expertise.
Conclusion
In conclusion, as we navigate through the complexities of securing our cloud environments on AWS, the importance of leveraging AWS’s infrastructure protection services cannot be overstated. From AWS Shield’s DDoS protection to AWS Network Firewall’s granular control over network traffic, these tools form the core of a strong defense-in-depth strategy. However, as threats evolve and become more sophisticated, so too must our approaches to infrastructure protection.
Generative AI presents a forward-thinking avenue to bolster our security postures. By integrating Generative AI into our security strategies, we can not only automate and accelerate threat detection and response but also enrich our decision-making processes with deeper insights and contextual analysis.
As you continue to explore and implement AWS’s infrastructure protection services, I encourage you to keep Generative AI in mind. Its potential to transform how we detect, analyze, and respond to security threats is immense, offering a proactive and intelligent layer of defense that can adapt to the ever-changing threat landscape.
Whether you’re just starting with AWS or looking to enhance your existing security measures, now is the time to dig deeper into both traditional security services and the innovative possibilities offered by Generative AI. By doing so, you’ll not only protect your infrastructure more effectively but also position yourself at the forefront of the next wave of security innovation on AWS. Stay curious, stay informed, and let’s embrace the future of infrastructure protection together.
