Here’s a revised title that is under 60 characters:
Boost Threat Detection with Amazon GuardDuty & Inspector
While AWS WAF and AWS Shield are powerful tools for web application security, a comprehensive security strategy requires broader threat detection and vulnerability assessment capabilities. In this article, we’ll explore how Amazon GuardDuty and Amazon Inspector can bolster your threat detection and management efforts. If you followed along in the last article in this series, you know have understanding the basics of AWS WAF and Shield. Let’s now dive into how Amazon GuardDuty can further enhance our security posture.
Setting Up Amazon GuardDuty
To enhance threat detection and security assessments, we’ll leverage Amazon GuardDuty and Amazon Inspector. From the AWS Console enable GuardDuty by clicking on “Get Started” on the GuardDuty landing page. You can see this in Figure 16:
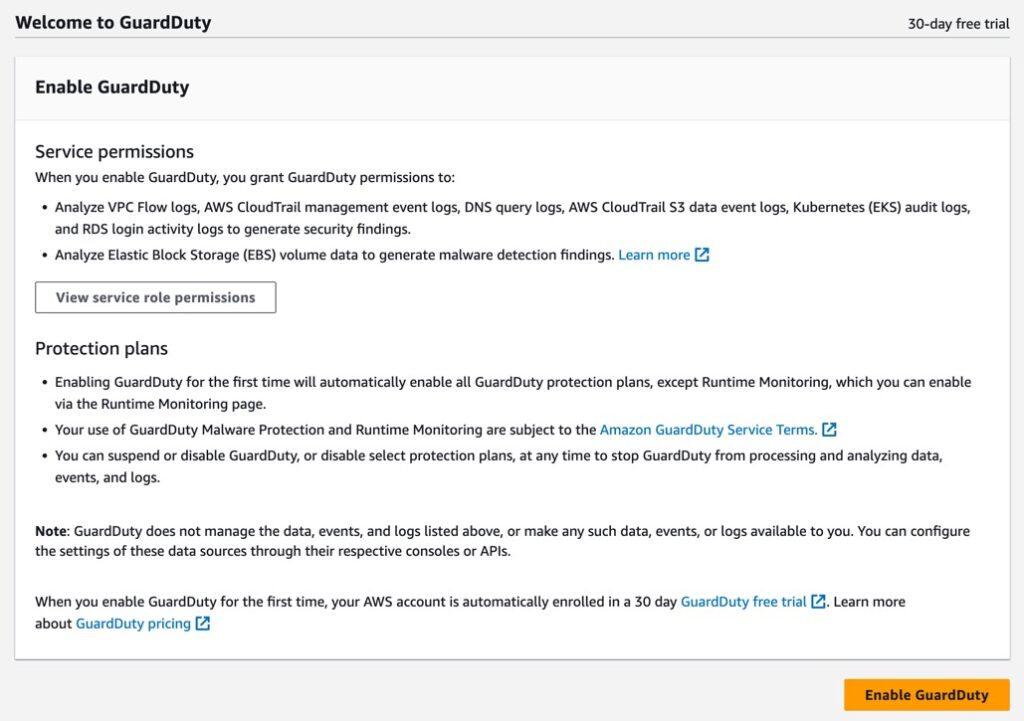
GuardDuty needs Service Permissions. It will set this up for you when you enable GuardDuty. The service permissions let GuardDuty analyze VPC Flow logs, AWS CloudTrail management event logs, DNS query logs, AWS CloudTrail S3 data event logs, Kubernetes (EKS) audit logs, and RDS login activity. It’s this data that GuardDuty users to generate findings. A finding is an event that GuardDuty thinks you should look at. The service permissions also let GuardDuty analyze Elastic Block Storage (EBS) volume data so it can generate malware detection findings. By turning on GuardDuty you get a 30 day trial in which all the protection plans except Runtime monitoring are enabled. Be sure to read all the details before clicking the Enable GuardDuty button. You can see this in Figure 2.
At this point GuardDuty will get to work. It will take some time before findings are generated and you can customize many settings using the menu on the left hand side. For now you’ll want to come back to the Summary page, see in figure 3, to see a list of findings.
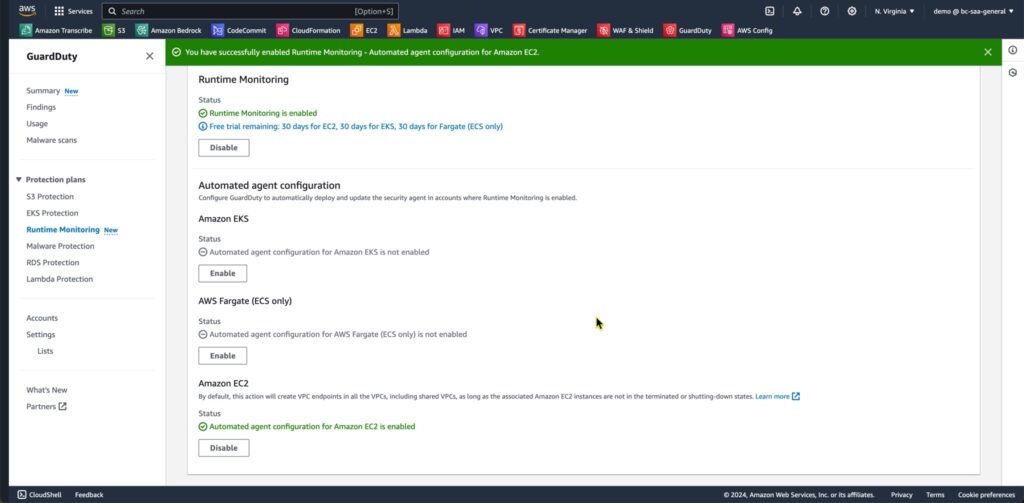
One last thing I want to do with GuardDuty is enable Runtime Monitoring for EC2 since I am running EC2 instances. Once GuardDuty is activated, it begins to monitor and analyze system logs. Let’s explore the types of findings GuardDuty can generate and what they mean for your security.
Understanding GuardDuty Findings
GuardDuty Runtime Monitoring for Amazon EC2 is a feature that provides real-time monitoring and threat detection for your EC2 instances. It analyzes the behavior of processes running on your instances, using machine learning models to identify potentially malicious or unauthorized activities. GuardDuty Runtime Monitoring can detect threats such as cryptocurrency mining, reverse shells, credential theft, and other malware or suspicious activities. It continuously inspects the runtime environment, including process execution, network activity, and file system changes, and generates findings for any detected threats, allowing you to quickly investigate and respond to potential security incidents within your EC2 environment. You can enable it in the Runtime Monitoring page on the left hand menu. For this to work you need to enable both Runtime monitoring and Amazon EC2 as seen in figure 4.
With GuardDuty monitoring in place, our next step is to strengthen our defenses with Amazon Inspector, which focuses on vulnerability management.
Enabling Amazon Inspector
With Inspector we get a 15-day trial. To get started we simply click the “Get Started” button. To enable Inspector click the Activate Inspector button as seen in figure 5. It may appear to be greyed out, but you can still click it.
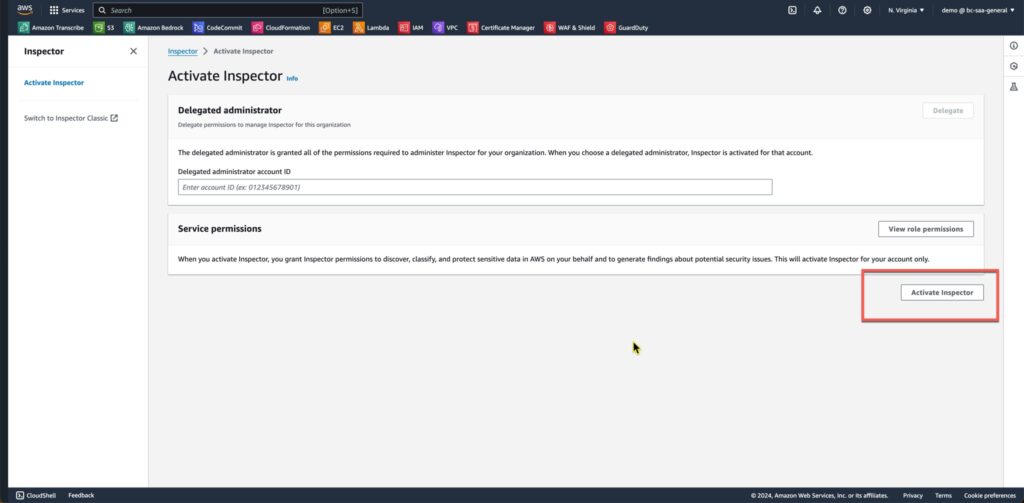
Once you enable inspector it will begin your fist scan. You can come back to the Dashboard page after the scan is complete and review the results.
Inspector will also prompt you to enable deep inspection of EC2 instances, seen in figure 6.

Since we are using EC2 I will enable this as well.
After setting up Inspector and starting our first scan, we’ll next review the vulnerabilities it uncovers.
Reviewing Inspector Results
After scanning we can see the instances we are currently monitoring, and this lines up with the two instances we created in our base architecture. These are listed in figure 7.
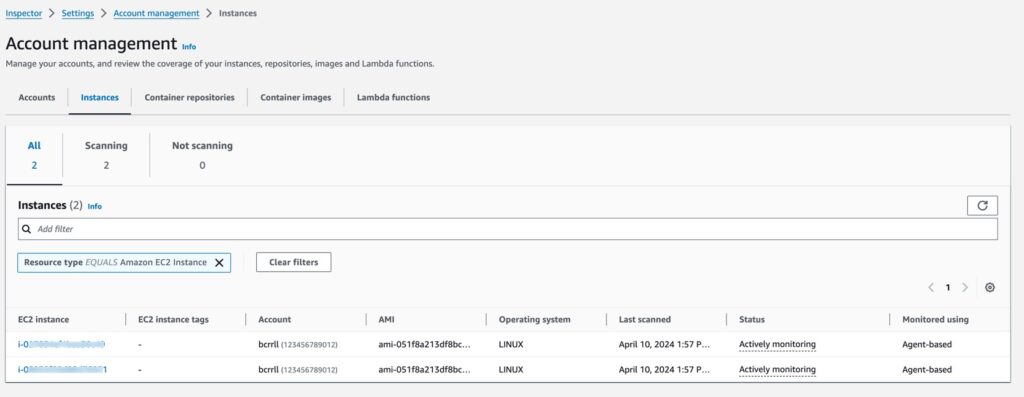
In this example, we enable Amazon GuardDuty to monitor our AWS environment for potential threats and malicious activities. We also initiate an Amazon Inspector assessment run to evaluate the security posture of our web application and identify potential vulnerabilities or deviations from best practices.
Having examined the detailed findings from Inspector, let’s conclude by discussing how integrating these tools with Amazon CloudWatch and AWS Config enhances overall security.
Conclusion: Enhancing Security with AWS Tools
By enabling Amazon GuardDuty and Amazon Inspector, you’ve added critical layers of threat detection and vulnerability assessment to your AWS environment. These services will continuously monitor for potential threats, malicious activities, and deviations from best practices, allowing you to proactively address security concerns.
At this point in our series, we’ve integrated Amazon GuardDuty and Amazon Inspector with our AWS setup that includes a VPC, ALB, and two EC2 instances, complemented by AWS WAF and Shield Advanced. GuardDuty enhances our ability to detect and respond to threats by continuously monitoring the environment and analyzing traffic and logs associated with our infrastructure. Meanwhile, Amazon Inspector helps identify vulnerabilities in the applications running on our EC2 instances by performing automated security assessments.
These tools are practical for maintaining strong security measures within your AWS environment, providing essential defenses against potential security threats. As we move forward in our series on Threat Detection and Management on AWS, we will continue exploring ways to effectively utilize AWS services to safeguard your infrastructure.
